Iptables is the default firewall used in many present Linux distros. It is a project under netfilter. Previously it was known as ipchains (For 2.2 Kernels) , ipfwadm(for 2.0 kernels) and nftables are their future project..Iptables are designed for ipv4 and ipv6table for ipv6.
From ipfwadm to iptables , we can see marginal modifications done in design and hence in features. In ipfwadm a rule set matched the packets and actions are taken on that packets , then in ipchains , chains are Incorporated and the rules will decide , through which chain the packets need to be traversed, then in iptables , tables are introduced so that the user can choose proper table based on his requirement , that means he can choose filter table for packet filtering . NAT tables for source and destination natting then mangle table for packet modifications.(We will discuss more about tables later ). Connection tracking capability is the yet another advancement with iptable. So we can say it as a statefull firewall. Rate limiting , system logging etc. are the other features included in iptables apart from it’s predecessors.
Iptables gets it’s ascendancy through the modularity and integrity with the kernel. It exploits the modularity of linux kernels. A bunch of kernel modules need to be loaded for the full operation of iptables.
ip_tables iptable_filter ip_conntrack ip_conntrack_ftp
iptable_nat ip_nat_ftp ipt_limit ipt_multiport
iptable_mangle ipt_state ipt_REJECT ipt_LOG
These are some of required kernel modules. All are not required for all applications. For loading modules in bootup add script in rc.local using modprobe command. And also we need a kernel with some specific config options .If it’s not there we need to recompile the kernel to exploit the functions of iptable. For latest kernels almost all options are included , rarely need to be recompiled. Some important options that need to be compiled in to kernel or as modules are
CONFIG_PACKET
CONFIG_NETFILTER
CONFIG_IP_NF_CONNTRACK
CONFIG_IP_NF_FTP
CONFIG_IP_NF_IRC
ONFIG_IP_NF_IPTABLES
CONFIG_IP_NF_FILTER
CONFIG_IP_NF_NAT
CONFIG_IP_NF_MATCH_STATE
CONFIG_IP_NF_TARGET_LOG
CONFIG_IP_NF_MATCH_LIMIT
CONFIG_IP_NF_TARGET_MASQUERADE .
You can check your current kernel configuration by cat /boot/config-`uname -r`.As I already told the latest kernels are incorporated with almost all netfilter options. So you seldom need to worry about that.
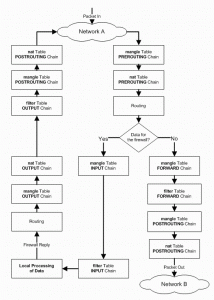
Packet flow in iptables
Next I would like to draw a vignette of packet flaw in iptables. There is definite order for traversing of packets through the different tables and chains in iptables. Basic understanding of that order is mandatory for writing complex firewall rules.
Iptable comprised of three tables , MANGLE , FILTER and NAT table.
Each tables have it’s own chains for packet processing.
MANGLE table : This tables is responsible for the alternation of QoS bits in TCP header.For example TOS (Type of service) bit. But it rarely used for simple networks.Mangle table have five chains ,PREROUTING, POSTROUTING,FORWARD,INPUT and OUTPUT.
FILTER table:This is the most used table in small network environments.This table is responsible for packet filtering on the basis of corresponding rules. This table have INPUT, FORWARD and OUTPUT chains. Most used target and jumps in this table are ACCEPT, DROP/DENY and REJECT. We will discuss about this target and jump later.
NAT table:This table used for network address translation which is a imperative feature of routers.It have PREROUTING chain (for Destination address translation) FORWARD chain (address translation for packets from router itself) and POSTROUTING chain( for source address translation).
When packet reaches the hardware(NIC) it will be processed to hardware driver and through kernel.Then it traverse through different tables and chains in the iptables in desired order. In each chain , iptable compare the rules in that chain with that packet information , if it finds a match then action is taken based on that rule.(eg:REJECT) .If a packet is matched with the first rule in a chain , it will not check the second rule in the same chain , it will jump to next chain in the order.
The following figure will help you to understand the packet traversal through iptable chains.
Options with iptable command.
-t Specify the table. By default FILTER table is taken .
-j Jump to the target
-A Append the rule to the end of the chain.
-F Flush. Deletes all the rules in the selected table
-p Match protocol. Types include, icmp, tcp, udp, and all
-s Match source IP address
-d Match destination IP address
-i Match “input” interface on which the packet enters.
-o Match “output” interface on which the packet exits
-m used to match certain conditions . eg: state ESTABLISHED
Targets and Jumps with iptable
DROP/DENY : When a packet is dropped or denied it is simply abandoned and no notification is send to the host. ie the packet disappears with out taking any further actions.
REJECT : The host reject the packet and sends reply to the sending host , saying that the packet was dropped. Other wise it is same as that of DROP/DENY.
ACCEPT : This will accept the packet that matches the corresponding rules.
LOG : The packet information will be logged with syslogd daemon.
SNAT : Source nat used in NAT table POSTROUTING table for manipulating source ip address.
DNAT: destination NAT used in NAT table PREROUTING table to manipulate destination ip address and for port forwarding.
MASQUERADE : To change source ip address to the ip address of corresponding router network interface.
Iptable commands and rules
iptables -L : To list all present rules in a table (By default it will show FILTER table rule.To specify the table use -t )
iptables -t nat -L (list all NAT table rules)
iptables -v -L : more detailed information about the rules
iptables -F
: it will flush all rules in that table. iptables -t table -D : to delete a particular rule from a tables’s chain. Or else we can give the rule number in that chain . eg: iptable -t nat -D PREROUTING 2 iptables -P : To set the default policy of a chain in FILTER table . eg: iptables -p OUPUT DROP Rule to allow only SSH traffic[bash]
iptables -A INPUT -p tcp -s 0/0 –dport 22 -j ACCEPT <This will allow port 22 on INPUT chain of filter table)
iptables-A OUTPUT -p tcp -m state –state ESTABLISHED,RELATED -j ACCEPT
iptables -P INPUT DROP
[/bash]
Rule for port forwarding[bash]
iptables -t nat -A PREROUTING -p tcp -d ‘destination ip’ –dport 80 -j DNAT –to-destination 192.168.1.10:80
Packet destined to 80 port of your public ip will be forwarded to the 80 port of private ip.We appending rule to the PREROUTING chain of NAT table.
iptables -A FORWARD -p tcp -s 0/0 -d 192.168.1.10 –dport 80 -j ACCEPT
[/bash]
I think this is enough for the basics. I will write more advanced rules on my next article. Try it!!!!!